Monitoring, control and security
Ermetix is a solution based on cloud (with Italian region) that allows you to manage any device based on Android, iOS, iPadOS, tvos and Windows, such as Smartphones, Handhelds, Tablets, Notebooks, PCs, Kiosks, Flat Panels: monitoring and controlling them remotely, protecting them from possible intrusions and the theft of the most valuable data, thanks to its module focused on defense against threats «mobile» (Mobile Threat Defense).
In particular, the protection of the device is delegated to specific algorithms that, thanks to the use of artificial intelligence, are able to block even sophisticated threats and/ or exploit unknown vulnerabilities, the so-called “ZERO DAY” vulnerabilities.
Moreover, Ermetix guarantees maximum flexibility of use, also thanks to the support of BYOD (Bring Your Own Device), COBO (Company Owned/Business Only) and COPE (Company Owned/Personally Enabled) management systems.
Distribution
Ermetix allows you to distribute apps, files and other resources to your organization’s devices, while ensuring optimal operation.
Control
Ermetix gives you a set of tools that can manage all the devices in your organization in an automated and granular way.
Monitoring
Thanks to its perfect integration with the various operating systems, Ermetix offers you a series of tools that allow you to monitor the main indicators of the devices of your organization allowing you, when necessary, to intervene remotely directly and in real time in the most disparate situations (e.g. theft, loss, viruses, etc…).
Protection
Thanks to sophisticated Mobile Threat Defense systems, based on Machine Learning, Ermetix can protect your organization’s devices both from known threats, such as Trojans and Ransonwares, and unknown threats (Zero Day Malwares), all complying with the requirements of the European regulation of the GDPR.

Distribution
Ermetix allows you to distribute and manage in an uniform way apps, APKs, EXE, MSI, file resources, certificates, settings and updates, ensuring a homogeneous and optimal operation over the entire “fleet” of devices.
Ermetix in fact allows you to access both the official stores, both through cloud repositories or alternative stores.
Official stores

Google Play Store

App Store

VPP Program
Microsoft Store
Cloud repository

Google Drive

Dropbox

OneDrive
Alternative stores

Aptoide
Control
Ermetix provides a series of simple tools that can manage your devices in a granular and efficient way in order to prevent any inappropriate use.
The Ermetix Dashboard, accessible via web browser from any device, allows you to create and manage policies and flows flexibly and quickly.
All work profiles, including restrictions and policies, can also be scheduled on an hourly basis through the simple and powerful programming module.

Monitoring
Ermetix provides you with tools to monitor and track device usage, reporting any malfunctions and allowing you to make more efficient the work of the staff as well as intervene remotely in case of loss or theft by geolacalizing the device itself and performing for example the remote wipe of data.
Maintenance
Real-time alerts on hardware operation and any anomalies
Screen display
Thanks to the screen display you can see and control Android devices remotely
Usage data collection
Access logs, app usage, connection log, and network traffic
Geolocalization
Workflows based on position
Protection
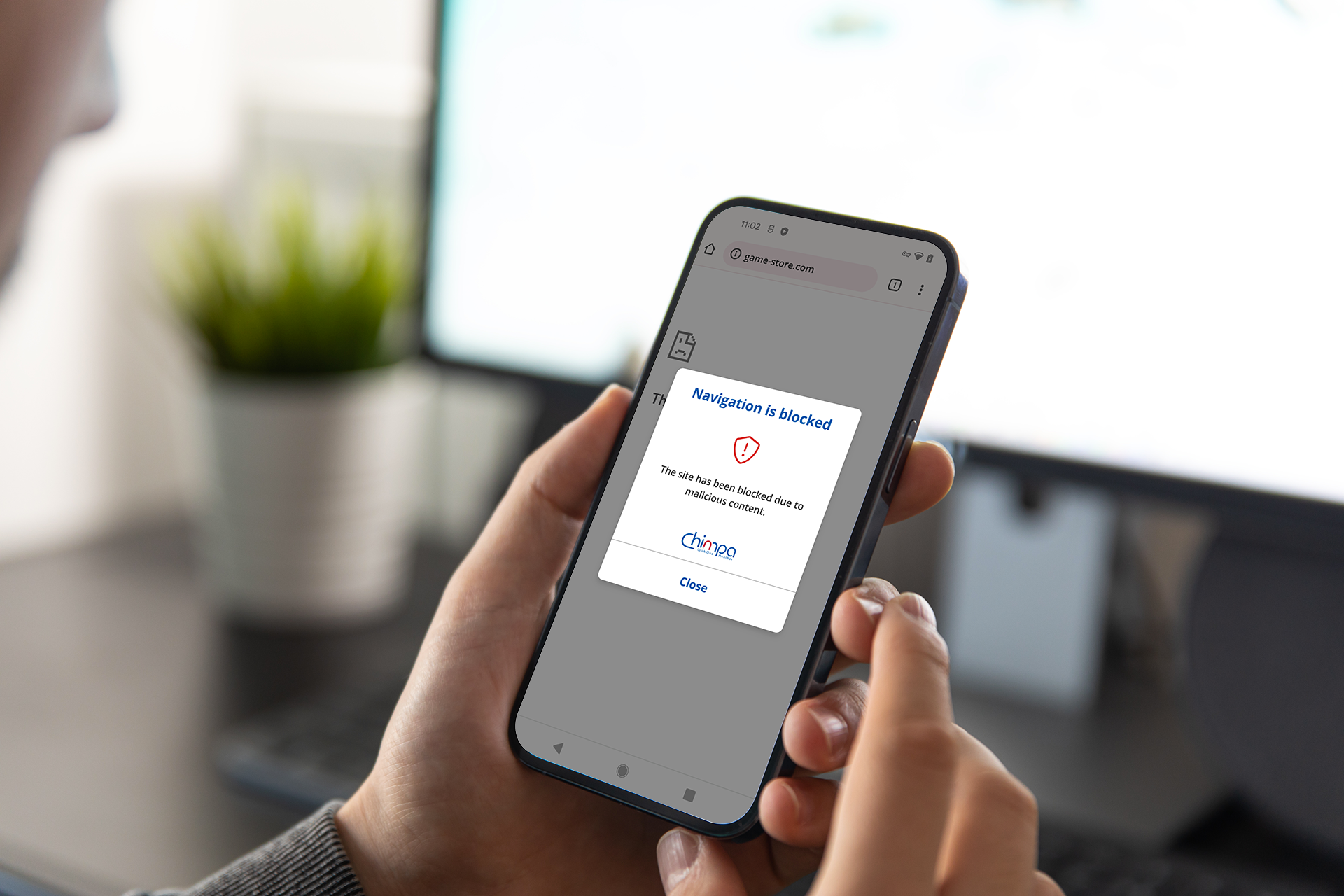
Ermetix protects your organization from improper use, knowingly and/or unaware, of devices by its staff, while complying with GDPR requirements by separating personal and business data.
Apps, data, information and business content are encrypted and protected by the MTD module, specially developed to defend data from threats such as Malware, Trojans and Ransomware that use the web (malicious sites), email (Phishing) or messaging (Smishing) as attack vectors.
Ermetix is also equipped with an advanced Cyber Threat Intelligence module, which, through the correlation of so-called compromise indicators (IOCs), is able to detect even unknown threats to date. The same module offers the possibility to do Open Source Intelligence (OSINT) activities on IP addresses, email and URL.